Four-Step Strategy to Modernise IAM Systems and Mitigate Unauthorised Access Risks Explained in New Blueprint From Info-Tech Research Group
A recently published research-backed blueprint from Info-Tech Research Group offers security leaders a comprehensive, proactive approach to modernising identity and access management (IAM) systems. To strengthen organisational security and operational efficiency in today's digital landscape, the firm's recently published resource emphasises the importance of developing a clear roadmap, building resilient IAM systems, and leveraging innovative solutions like decentralised identity.
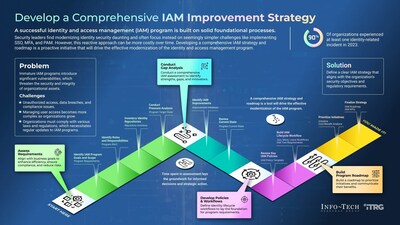
SYDNEY, Jan. 21, 2025 /PRNewswire/ -- Organisations around the world are becoming increasingly vulnerable to unauthorised access and compliance gaps within their identity and access management (IAM) systems, highlighting the need for a proactive approach to safeguarding digital assets. In response to these growing challenges, Info-Tech Research Group has recently released its blueprint, Develop a Comprehensive IAM Improvement Strategy, to provide security leaders with comprehensive and timely IAM improvement strategies that align security objectives with regulatory requirements. The proactive approach mentioned in the firm's new resource not only enhances security but also equips security leaders to navigate the complexities of modern cybersecurity with confidence and resilience.
'A comprehensive identity and access management (IAM) program can enhance an organisation's security and operational efficiency. However, IAM programs are challenging to implement,' says Michel Hébert, principal research director at Info-Tech Research Group. 'Practitioners must collaborate with stakeholders to integrate systems, applications, and directories; address technical debt and outdated infrastructure; and balance robust security measures with a seamless user experience.'
The recently published resource from Info-Tech outlines common challenges faced by organisations in managing their IAM programs, including complexity, scalability, and cross-departmental collaboration. The firm notes that integrating multiple systems, applications, and directories can be especially difficult, particularly for organisations with large, complex IT environments. Resilience is also essential; as organisations evolve, IAM systems must scale to support more users, changing access needs, and new technologies like cloud services and mobile devices.
Info-Tech's Key Steps for Building a Comprehensive IAM Strategy
In Develop a Comprehensive IAM Improvement Strategy, Info-Tech details a strategic four-step process that guides security leaders in implementing an effective IAM program. These steps ensure that organisations can enhance security, optimise processes, and align IAM initiatives with business goals:
Step 1: Assess Requirements – Align IAM goals with business objectives to enhance efficiency, ensure compliance, and reduce risks.
Step 2: Conduct Gap Analysis – Perform a comprehensive IAM assessment to identify strengths, gaps, and opportunities for improvement.
Step 3: Develop Policies & Workflows – Establish identity lifecycle workflows to lay the groundwork for program requirements and ensure that requirements are met.
Step 4: Build Program Roadmap – Prioritise IAM initiatives and communicate their benefits to stakeholders through a clear, actionable roadmap.
Info-Tech's comprehensive resource emphasises that security leaders should focus on proactive IAM modernisation rather than reactive solutions like single sign-on (SSO), multifactor authentication (MFA), and privileged access management (PAM). By taking a more comprehensive approach, organisations can create a resilient IAM system that aligns with their long-term security and business goals.
This new blueprint will provide security leaders with the strategic insights required to strengthen their IAM systems, ensure compliance, and enhance overall operational efficiency. In the resource, the firm highlights that clear communication and stakeholder engagement are critical for successful implementation, as IAM programs often require phased rollouts to deliver value over time.
For exclusive and timely commentary from Info-Tech's experts and analysts, including Michel Hébert, an expert in security and privacy practices, and access to the complete Develop a Comprehensive IAM Improvement Strategy blueprint, please contact pr@infotech.com.
Info-Tech LIVE 2025 in Australia IT Conference
Registration is now open for Info-Tech LIVE 2025 in Australia, taking place March 18 to 19, 2025, in Brisbane, Australia. This premier event offers journalists, podcasters, and media influencers access to exclusive content, the latest IT research and trends, and the opportunity to interview industry experts, analysts, and speakers. To apply for media passes to attend the event or gain access to research and expert insights on trending topics, please contact pr@infotech.com.
About Info-Tech Research Group
Info-Tech Research Group is one of the world's leading research and advisory firms, proudly serving over 30,000 IT and HR professionals. The company produces unbiased, highly relevant research and provides advisory services to help leaders make strategic, timely, and well-informed decisions. For nearly 30 years, Info-Tech has partnered closely with teams to provide them with everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organisations.
To learn more about Info-Tech's divisions, visit McLean & Company for HR research and advisory services and SoftwareReviews for software buying insights.
Media professionals can register for unrestricted access to research across IT, HR, and software and hundreds of industry analysts through the firm's Media Insiders program. To gain access, contact pr@infotech.com.
For information about Info-Tech Research Group or to access the latest research, visit infotech.com and connect via LinkedIn and X.

Photo - https://mma.prnewswire.com/media/2602102/Info_Tech_Research_Group_Four_Step_Strategy_to_Modernise_IAM_Sys.jpg
Logo - https://mma.prnewswire.com/media/2602101/Info_Tech_Research_Group_Four_Step_Strategy_to_Modernise_IAM_Sys.jpg
Media Contact: Sufyan Al-Hassan, Senior PR Manager, Info-Tech Research Group, salhassan@infotech.com | +1 (888) 670-8889 x2418
SOURCE Info-Tech Research Group

